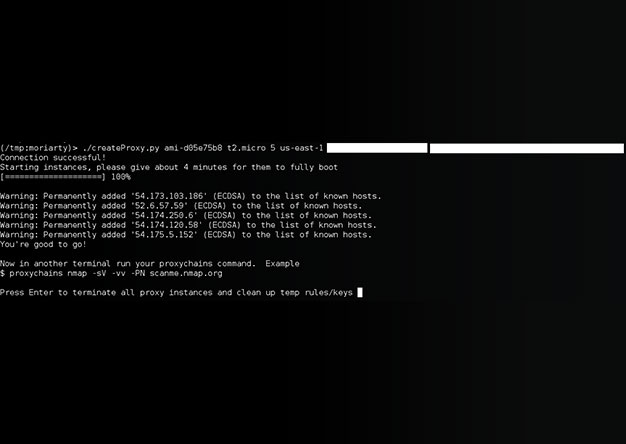
Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...
Exploring Initial Access Methods #01 – Shortcuts and Tunnels to the Kingdom
read more
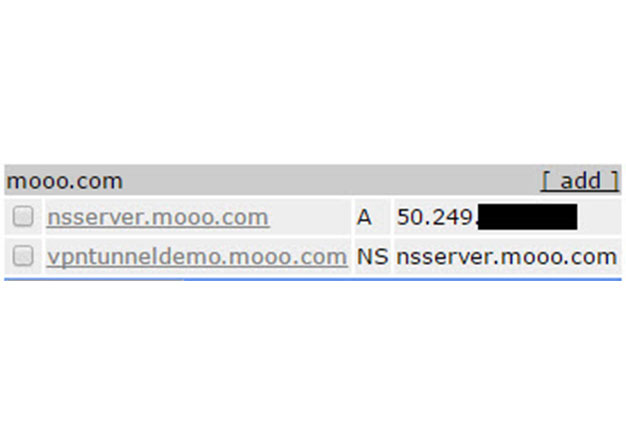
![[UPDATE] Creating your own private botnet for scanning.](https://www.synercomm.com/wp-content/uploads/2015/09/B87Im1.jpg)