During the post exploitation phase of a penetration test, I like to provide the client with examples of what could happen if a breach were to take place. One of the most common examples of this is...
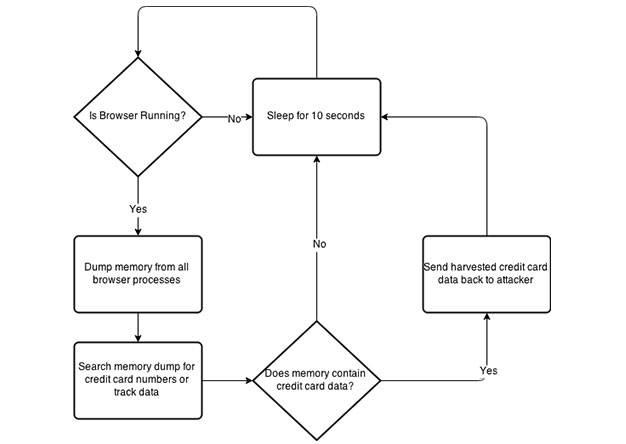
PowerShell Memory Scraping for Credit Cards
read more