I recently started learning about the world of game modding. I have always played games on a console, so modding was not something I ever pursued. However, after picking up the PC version of my...


I recently started learning about the world of game modding. I have always played games on a console, so modding was not something I ever pursued. However, after picking up the PC version of my...

One of the popular methods for dumping LSASS is using the procdump.exe program from the Sysinternals Suite. Something like: procdump64.exe -accepteula -ma -o dumpfile.dmp However, Microsoft is well...
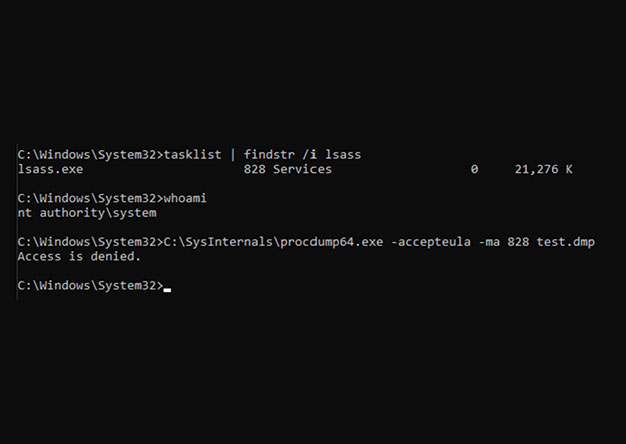
In my last blog post, I discussed one method of dumping LSASS where we created a DLL that we injected into Task Manager. We could then create an LSASS dump from Task Manager, and the DLL would hook...

Intro Disclaimer: this research is intended exclusively as an intellectual exercise and a means of making defenders aware of the simple possibilities with Rust malware. Using any of the provided...

In penetration testing, it’s important to have an accurate scope and even more important to stick to it. This can be simple when the scope is limited to a company’s internet service provider (ISP)...
On August 15th, 2018 a vulnerability was posted on the OSS-Security list. This post explained that OpenSSH (all versions prior to and including 7.7) is vulnerable to username enumeration by sending...

In the hit Netflix series 'Stranger Things', the Upside Down is the parallel dimension inhabited by a monster. It is a dark and cold reflection of the dimension inhabited by humans, containing the...
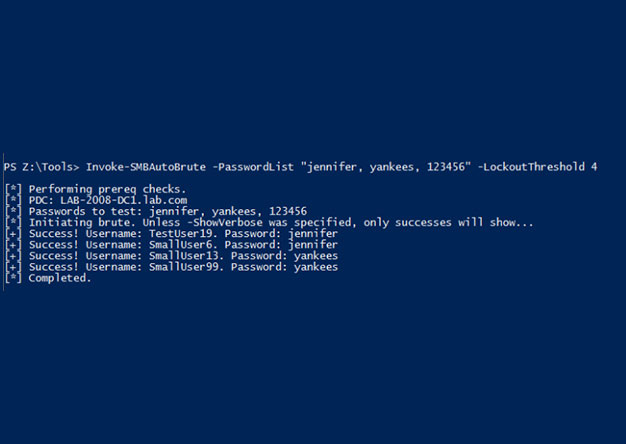
Intro One of my favorite post-ex metasploit modules is smb_login. It's great for running a quick test using credentials you've discovered. One of the problems with it is that there is nothing that...
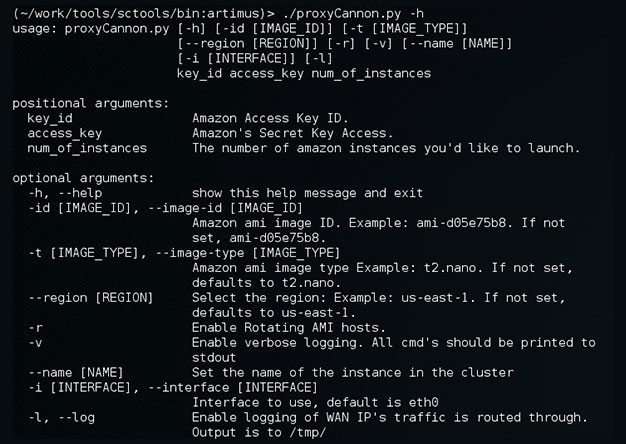
ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result, there's some new features we'd like to introduce. Cleaner User Interface We've cleaned...
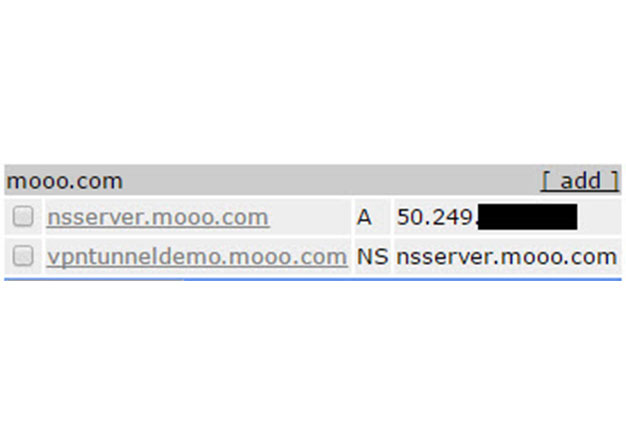
Overview For some time now, we've been using DNSCat as a means to covertly transmit data during engagements where clients IDS's or Firewalls might otherwise block us. The DNS protocol is often...