One of the greatest yet unknown dangers that face any cloud-based application is the combination of an SSRF vulnerability and the AWS Metadata endpoint. As this write up from Brian Krebbs explains,...
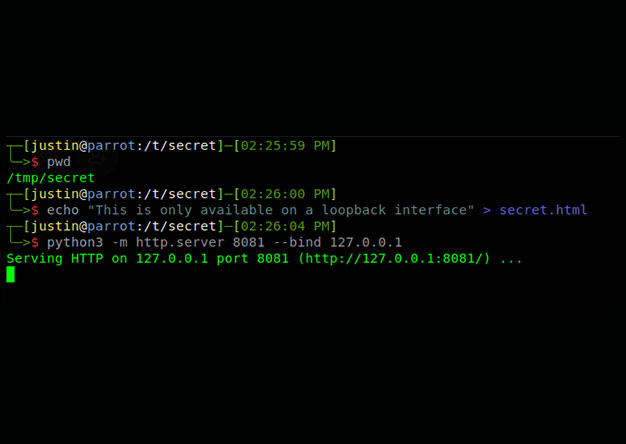

One of the greatest yet unknown dangers that face any cloud-based application is the combination of an SSRF vulnerability and the AWS Metadata endpoint. As this write up from Brian Krebbs explains,...
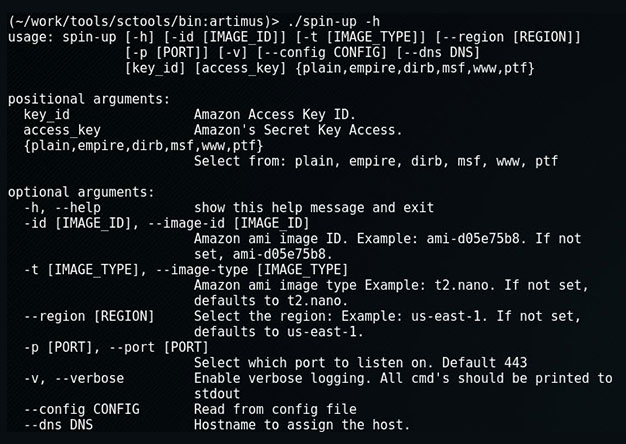
When on an engagement, sometimes we'll encounter an eager blue team hellbent on identify and blocking our attacks. Typical in those instances we'd use proxy-cannon and route through multiple (ever...
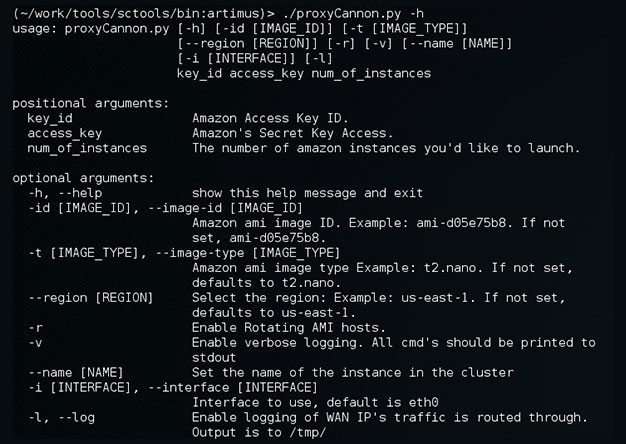
ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result, there's some new features we'd like to introduce. Cleaner User Interface We've cleaned...
![[UPDATE] Creating your own private botnet for scanning.](https://www.synercomm.com/wp-content/uploads/2015/09/B87Im1.jpg)
This is an update to an older post that can be found here. Since createProxy's initial release, we've received some great feedback and, as a result, we made some improvements. There were several...
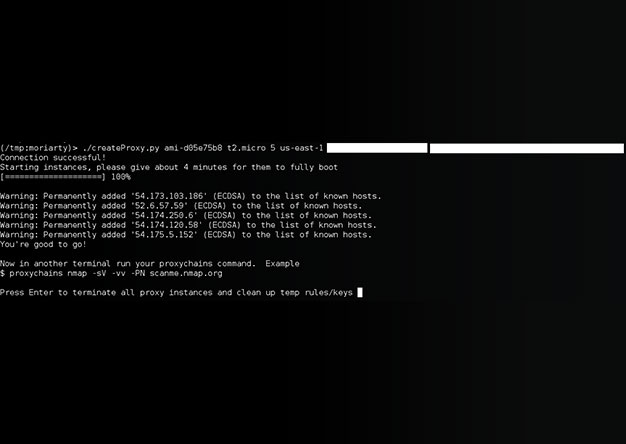
[ UPDATE] The tool has been re-written. New details can be found here: http://www.shellntel.com/blog/2015/9/9/update-creating-your-own-private-botnet-for-scanning Often while scanning a network...