Resources
How to Approach the General Data Protection Regulation (GDPR) With a Security Framework
GDPR has been in place since May 25th, 2018 and has already been used in legal actions against companies, with over 200,000 cases reported within this first year. The law is expected to make a...
Framework or Crash, the Choice is Yours!
Are you using a framework to establish your information security program? If not, I get it; it’s complicated. On a second thought, have you lost your mind? I’ve been there. A number of years ago,...
Lessons Learned from Pentesting – What Should Keep You Up At Night
Coming from someone who can officially say that information security has given me a few gray hairs, I'm writing this article from the perspective of someone who's been around the block. With over 15...
Characteristics of a Relevant Information Security Program: Communications
The Challenge You budget for, enable, and staff your organization’s information security program with people, technology, and visionary prowess. As you step back and observe do you find yourself...
Why 14 Characters?
Background While experts have agreed for decades that passwords are a weak method of authentication, their convenience and low cost has kept them around. Until we stop using passwords or start using...

How to build a (2nd) 8 GPU password cracker
Why? … Stop asking questions! Background In February 2017, we took our first shot at upgrading our old open-frame 6 GPU cracker (NVIDIA 970). It served us well, but we needed to crack 8 and...
DA 101 – Protecting your Domain Admin Account
At SynerComm's Fall IT Summit 2018 we presented a talk about the top 5 attacks used to compromise a Domain Administrator account. As a short recap, the top five are the following: 1.Permissive...
OpenSSH < 7.7 - Username Enumeration Exploit
On August 15th, 2018 a vulnerability was posted on the OSS-Security list. This post explained that OpenSSH (all versions prior to and including 7.7) is vulnerable to username enumeration by sending...
Thoughts on Blocking Powershell.exe
This post is inspired by a twitter debate I observed between a pentester and a defender. It's characteristic of several such debates I've seen on this topic. The debate goes something like this:...

How to build a 8 GPU password cracker
TL;DR This build doesn't require any "black magic" or hours of frustration like desktop components do. If you follow this blog and its parts list, you'll have a working rig in 3 hours. These...

The Upside Down – Ventures into the 5GHZ Spectrum
In the hit Netflix series 'Stranger Things', the Upside Down is the parallel dimension inhabited by a monster. It is a dark and cold reflection of the dimension inhabited by humans, containing the...
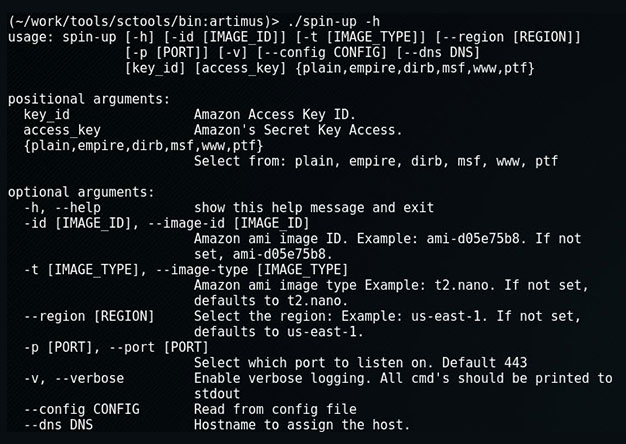
Spin-up: Quickly Launch a Provisioned EC2 Attack Server
When on an engagement, sometimes we'll encounter an eager blue team hellbent on identify and blocking our attacks. Typical in those instances we'd use proxy-cannon and route through multiple (ever...
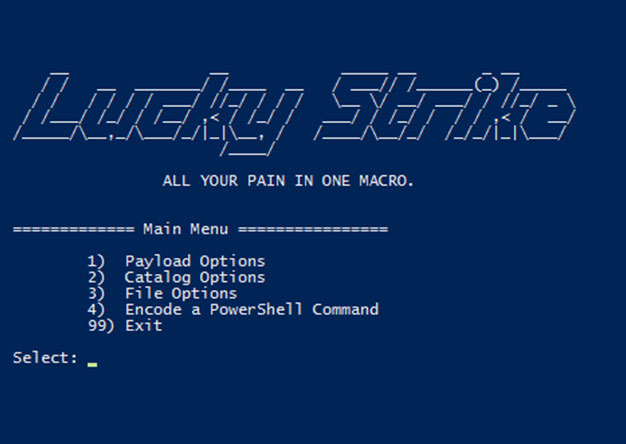
Luckystrike: An Evil Office Document Generator.
DerbyCon Tool Drop 2.0 Talk here. Luckystrike demo begins at 18:45. <tldr> Luckystrike is a PowerShell based generator of malicious .xls documents (soon to be .doc). All your payloads are...

The Number One Pentesting Tool You’re Not Using
TL;DR: Reporting sucks, rarely does anyone enjoy it. Serpico is a tool that helps with reporting and makes it suck less through collaboration and automation, saving you time that you’d rather spend...
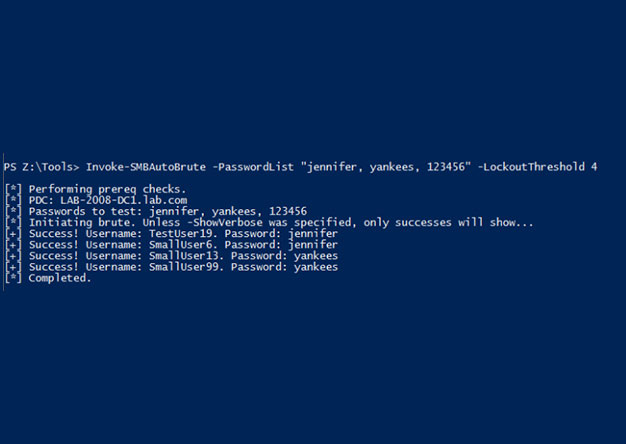
Invoke-SMBAutoBrute.ps1 – Smart SMB Brute Forcing
Intro One of my favorite post-ex metasploit modules is smb_login. It's great for running a quick test using credentials you've discovered. One of the problems with it is that there is nothing that...