Resources

SynerComm Reboots a Security Staple with ‘Continuous’ Pentesting
Participating in Black Hat USA 2020, we sat down with Dark Reading where our own Brian Judd, VP Information Assurance discusses how we are innovating and evolving penetration testing. See more at...

Incorporating Your Lessons Learned for Pandemic Contingency Planning Considerations
Although contingency planning has a healthy focus on technology, it still requires people to interface with that technology, configure and program the technology so that it will perform some...
We’ll get through this; how will it make us stronger? Make COVID-19 “lessons learned” a priority
The COVID-19 event, obviously, has had a wide-reaching negative impact for the entire country. Despite this, even in the face of the trauma linked to the loss of loved ones, we will eventually...

Building a Pwnagotchi
What is a Pwnagotchi? From the Website: Pwnagotchi is an A2C-based “AI” powered by bettercap and running on a Raspberry Pi Zero W that learns from its surrounding WiFi environment in order to...

Continuous Penetration Testing
“So, let’s say we fix all of the vulnerabilities that the pentest discovers… How do we know tomorrow that we’re not vulnerable to something new?” ~Customer Bridging the Gap Between...

People are People, but Where Can You Find Them When You Need Them?
Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully overcome that challenge every day, and so I suppose I suffer from the old adage: “to a...
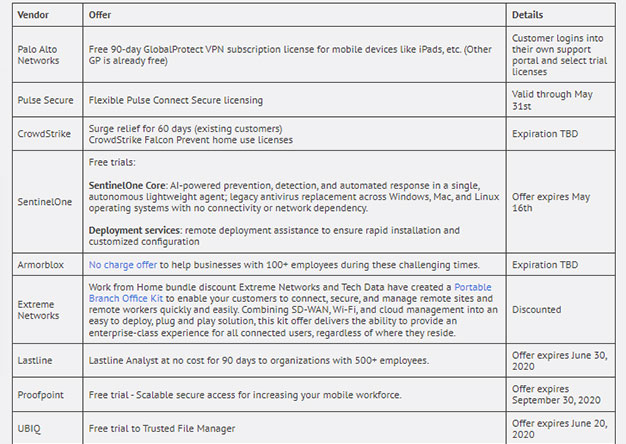
Vendors Stepping Up in a Time of Need
Most enterprises are getting slammed with employees working from home. Most of us designed our remote user VPN’s for the occasional "snow day" ...right. Now we have an entire workforce, working from...
Remote Access Rush
Practicing good remote access hygiene in times of uncertainty As the business world reacts to the current health crisis, companies are offering remote access to any role that can work from home....
Are we prepared?
Risks and Considerations for IT: A Pandemic What can IT do to prepare? We all know the stats of the Coronavirus, although they are changing by the minute. We know what to do personally and for our...

Stop Sharing Your Password with Everyone
Insert under image - Palo Alto Networks firewalls have the ability to create security policies and generate logs based on users and groups, and not just IP addresses. This functionality is called...
Cybersecurity Maturity Model Certification (CMMC)
From a quick assessment on what has been published thus far on the CMMC regulation and its overall goal, it appears that contractors lack of information security will no longer be tolerated by the...
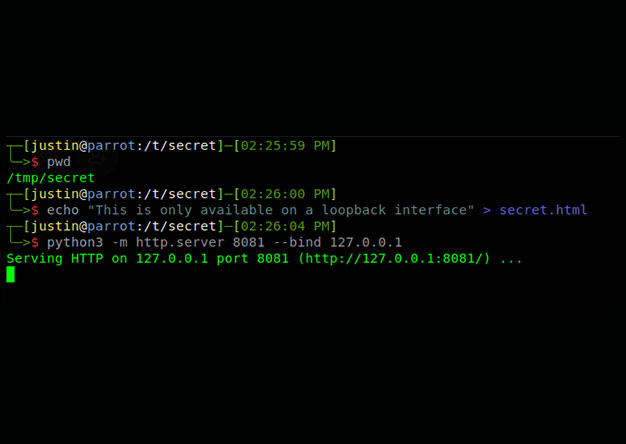
AWS Metadata Endpoint – How to Not Get Pwned like Capital One
One of the greatest yet unknown dangers that face any cloud-based application is the combination of an SSRF vulnerability and the AWS Metadata endpoint. As this write up from Brian Krebbs explains,...
Understanding HIPAA: PHI and Covered Entities
Medical community challenge: In a business environment where resources are limited, compliance requirements abound, and budgets are constantly challenged to meet cost containment targets, the...
Understanding HIPAA: Starting with the Rules
Medical community challenge: In a business environment where resources are limited, compliance requirements abound, and budgets are constantly struggling to meet cost containment targets, the...
Why Microsoft Office 365 Secure Score Isn’t Enough
Microsoft Secure Score. If you’re an IT administrator or security professional in an organization that uses Office 365, then you’ve no doubt used the tool or at least heard the term. It started as...