Resources

AI and Machine Learning in Threat Detection: Navigating Advancements and Challenges (Part 2)
In part one of this series, we discussed the evolving landscape of cybersecurity and the roles artificial intelligence (AI) and machine learning (ML) play in the security space today. Here in part...

Beyond Vulnerability Scanning: Strengthening Perimeter Cybersecurity
Over the past 20-years, I’ve used every major vulnerability scanner. There are several great scanners on the market, and SynerComm has continually used one of them from its free GNU public license...

AI and Machine Learning in Threat Detection: Navigating Advancements and Challenges (Part 1)
With the help of artificial intelligence (AI) and machine learning (ML), cybercriminals are creating novel, sophisticated threats more frequently and with fewer resources than ever before. These...

Attacks on Active Directory Certificate Services (AD CS) Explained – CypherCon 2024 Follow-up
This is a follow-up blog post from our CypherCon 2024 presentation. The slides are located here: https://x.com/TheL0singEdge/status/1776101737461399780 Active Directory Certificate Services (AD CS)...
Exploring Initial Access Methods #01 – Shortcuts and Tunnels to the Kingdom
Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial access to systems is crucial for developing robust defense mechanisms. Initial access...

Continuous Pentesting and Its Many Names
Are you looking for a pentest? A continuous pentest? Or maybe attack surface management? We’ll never have a shortage of new terminology (and acronyms) to learn and understand. When evaluating...
Strengthening Healthcare Defenses
In the dynamic realm of cybersecurity, the healthcare industry has become a prime target for malicious actors seeking to exploit vulnerabilities and gain unauthorized access to sensitive data....

Spoofing Command Line Arguments to Dump LSASS in Rust
One of the popular methods for dumping LSASS is using the procdump.exe program from the Sysinternals Suite. Something like: procdump64.exe -accepteula -ma -o dumpfile.dmp However, Microsoft is well...

The Future of Business Applications and Data Center Access: Insights from SynerComm’s IT Summit
The recent 20th Anniversary of IT Summit was an eye-opener for tech enthusiasts, security professionals, and business leaders alike. This annual two-day event brings together IT leaders from across...

Navigating the Skies: TSA’s New Cybersecurity Requirements for Airlines
In today's increasingly digital world, the aviation industry is more reliant on technology than ever before. As aviation systems become more connected and dependent on the internet, the risk of...
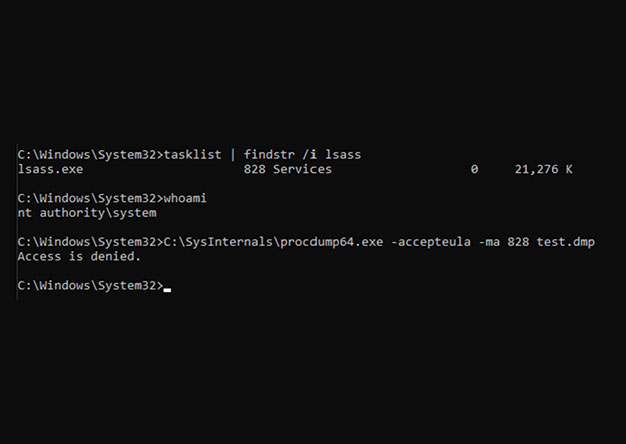
Creating a Rootkit to Inject into a Protected Process and Dump LSASS
In my last blog post, I discussed one method of dumping LSASS where we created a DLL that we injected into Task Manager. We could then create an LSASS dump from Task Manager, and the DLL would hook...

DEF CON 31 and Building A Wi-Fi Deauthentication Detector
Going to DEF CON was a dream I never thought would come to fruition. I remember 2009 being in 8th grade. Reading a physical copy of the magazine Wired. Sitting in the back of parent's minivan on the...

Rotating Your Pentesting Vendor Is A Mistake!
Having sold and performed assessments and pentests for nearly 20 years, I’ve had plenty of opportunities to hone my strategy and messaging. One common challenge I hear is, “our Board of Directors...
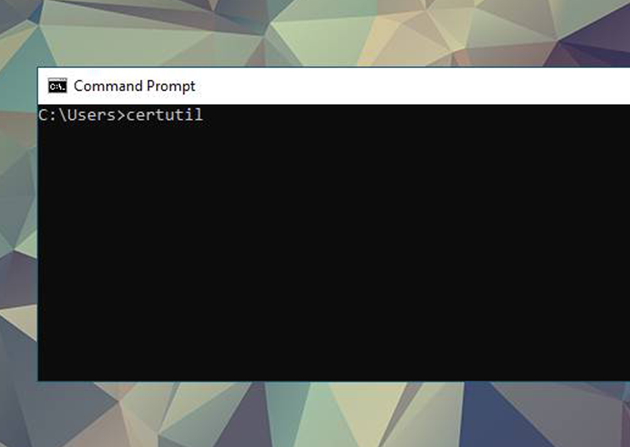
Fun with AD CS from Windows Command Line
I’m a fan of full featured and weaponized C2s as much as anyone else to save time if it makes my job easier. Sometimes they can make your job harder when you’re dealing with EDR. A lot of opsec...

Common Cybersecurity Pitfalls to Avoid in 2023
In today’s business world, most companies are fully reliant on technology to maintain their daily operations. Data has become valuable currency and as much as technology creates convenience and...