Once in a blue moon we come across a client that has truly done security right (or at least, tried really hard to do so). All the low hanging fruit has been trimmed: Responder doesn't work, no...
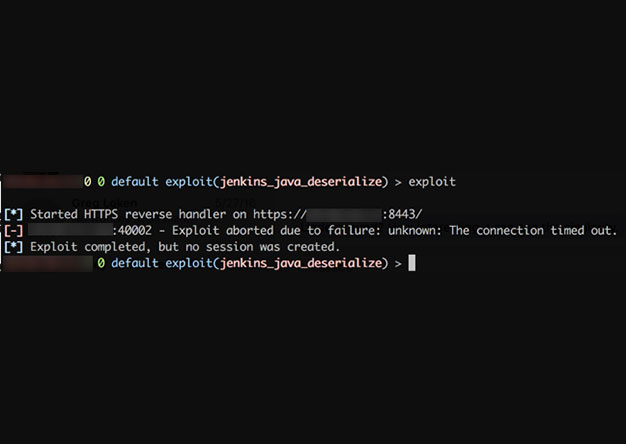

Once in a blue moon we come across a client that has truly done security right (or at least, tried really hard to do so). All the low hanging fruit has been trimmed: Responder doesn't work, no...
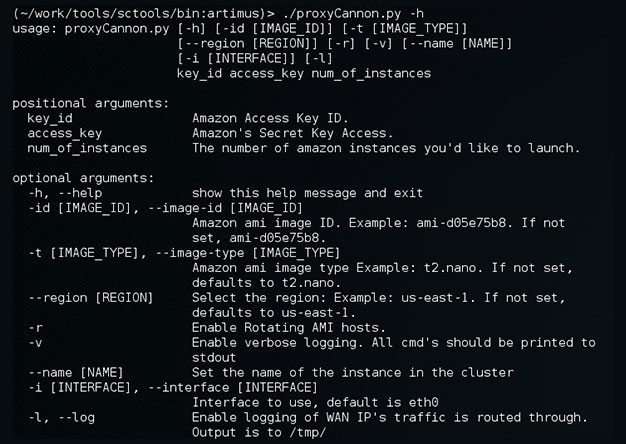
ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result, there's some new features we'd like to introduce. Cleaner User Interface We've cleaned...
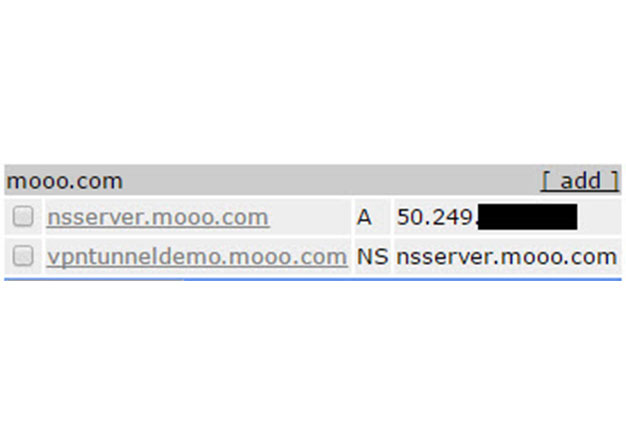
Overview For some time now, we've been using DNSCat as a means to covertly transmit data during engagements where clients IDS's or Firewalls might otherwise block us. The DNS protocol is often...
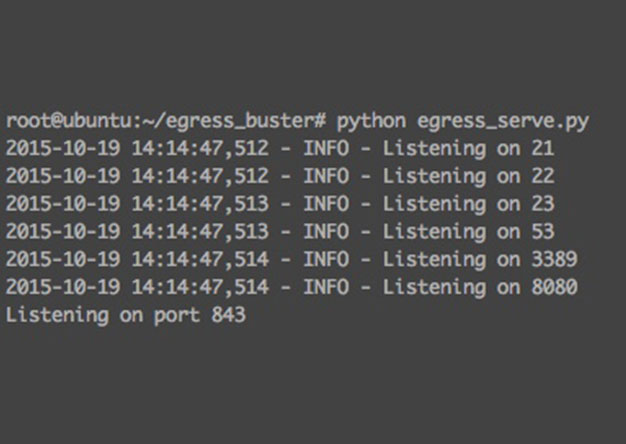
Problem It is common during a penetration test that a tester may run into the problem of figuring out which ports and maybe even which protocols are allowed out of an environment. This is due to the...
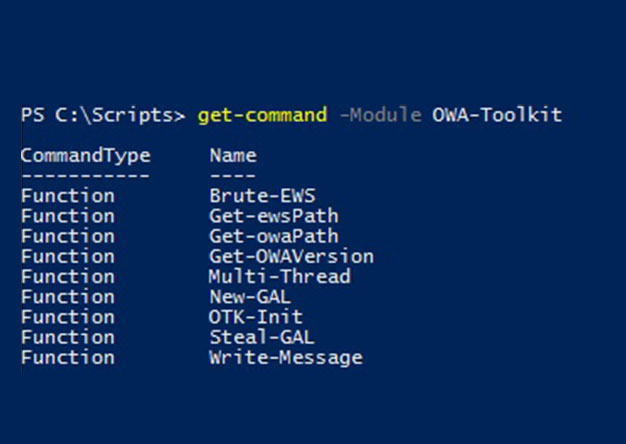
Outlook Web Access (OWA) has been one of the consistently viable attack vectors for pentesters and bad guys alike for many years. Frequently, an attacker will obtain valid credentials by brute...

First, let's talk about what "failure" is and is not in the context of Security Awareness Training (SAT). Failure is not when a company gets breached due to social engineering. Wait, what?? All the...

Very frequently during a web application assessment a pentester may begin by fingerprinting what web frameworks and libraries are used by a given application. Possibly by running a tool such as...
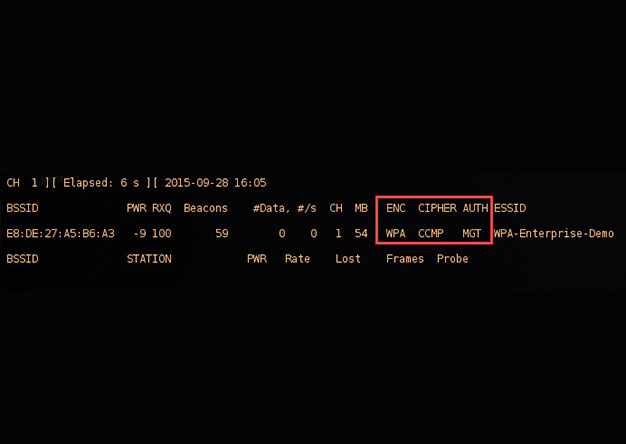
With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically, enterprise wireless networks employ WPA-Enterprise security features, which removes...
![[UPDATE] Creating your own private botnet for scanning.](https://www.synercomm.com/wp-content/uploads/2015/09/B87Im1.jpg)
This is an update to an older post that can be found here. Since createProxy's initial release, we've received some great feedback and, as a result, we made some improvements. There were several...
Recently some of us here at shellntel have been building quadcopters and autonomous vehicles for fun. We are big fans of the Pixhawk flight controller for its awesome autonomous capabilities. We...