Intro Disclaimer: this research is intended exclusively as an intellectual exercise and a means of making defenders aware of the simple possibilities with Rust malware. Using any of the provided...


Intro Disclaimer: this research is intended exclusively as an intellectual exercise and a means of making defenders aware of the simple possibilities with Rust malware. Using any of the provided...

What is Lucee? Lucee is an open-source Cold Fusion Markup Language (CFML) application server and engine intended for rapid development and deployment. It provides a lot of out of the box...

In February 2017, I co-authored a blog detailing our build of an 8-GPU password cracker. Over the past 8 years, it’s had millions of views and thousands of comments. To all the concerned writers,...

I can remember it like it was yesterday... Casey, Hans, Jason, Scott, Sam, Bill and I were slowly destroying my hotel suite at Circle City Con while trying to win the 2015 CTF. (We took 2nd place...

Whether doing security research or troubleshooting networks, network sniffers and packet analysis can be invaluable tools. If you're a network engineer like me, you've probably been holding onto...

In penetration testing, it’s important to have an accurate scope and even more important to stick to it. This can be simple when the scope is limited to a company’s internet service provider (ISP)...

What is a Pwnagotchi? From the Website: Pwnagotchi is an A2C-based “AI” powered by bettercap and running on a Raspberry Pi Zero W that learns from its surrounding WiFi environment in order to...

Insert under image - Palo Alto Networks firewalls have the ability to create security policies and generate logs based on users and groups, and not just IP addresses. This functionality is called...
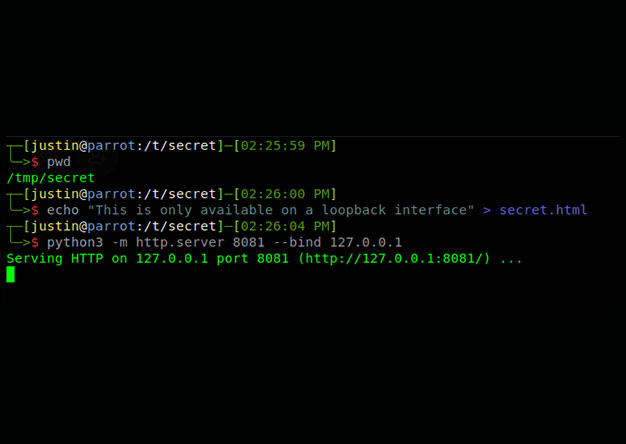
One of the greatest yet unknown dangers that face any cloud-based application is the combination of an SSRF vulnerability and the AWS Metadata endpoint. As this write up from Brian Krebbs explains,...
Background While experts have agreed for decades that passwords are a weak method of authentication, their convenience and low cost has kept them around. Until we stop using passwords or start using...