Meet CASM®
The New Face of Managed Vulnerability Scanning
Out with the old and in with the new: Continuous Attack Surface Management (CASM) takes the guesswork out of security, automates asset discovery, and monitors while validating risk with expert analysts.
Learn how CASM protects your company and client data.
CASM arms you with information you need to safeguard your IT infrastructure.
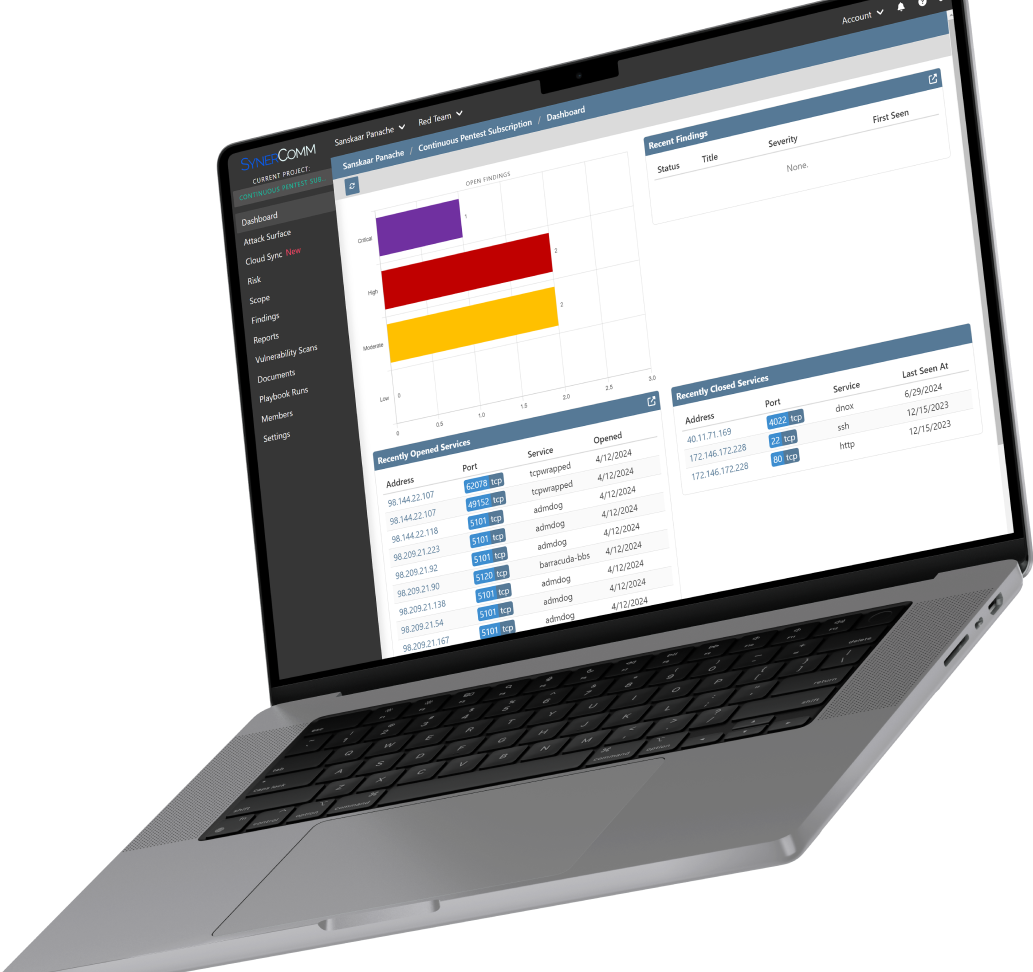
CASM automates the discovery, monitoring, and analysis of risks and vulnerabilities within your external attack surface. This unified solution addresses needs ranging across vulnerability management, attack surface management, compliance, asset inventory and more.
CASM is designed to accurately discover assets and monitor public attack surfaces. It combines powerful discovery and penetration testing tools and data sources into a single, user-friendly query dashboard.
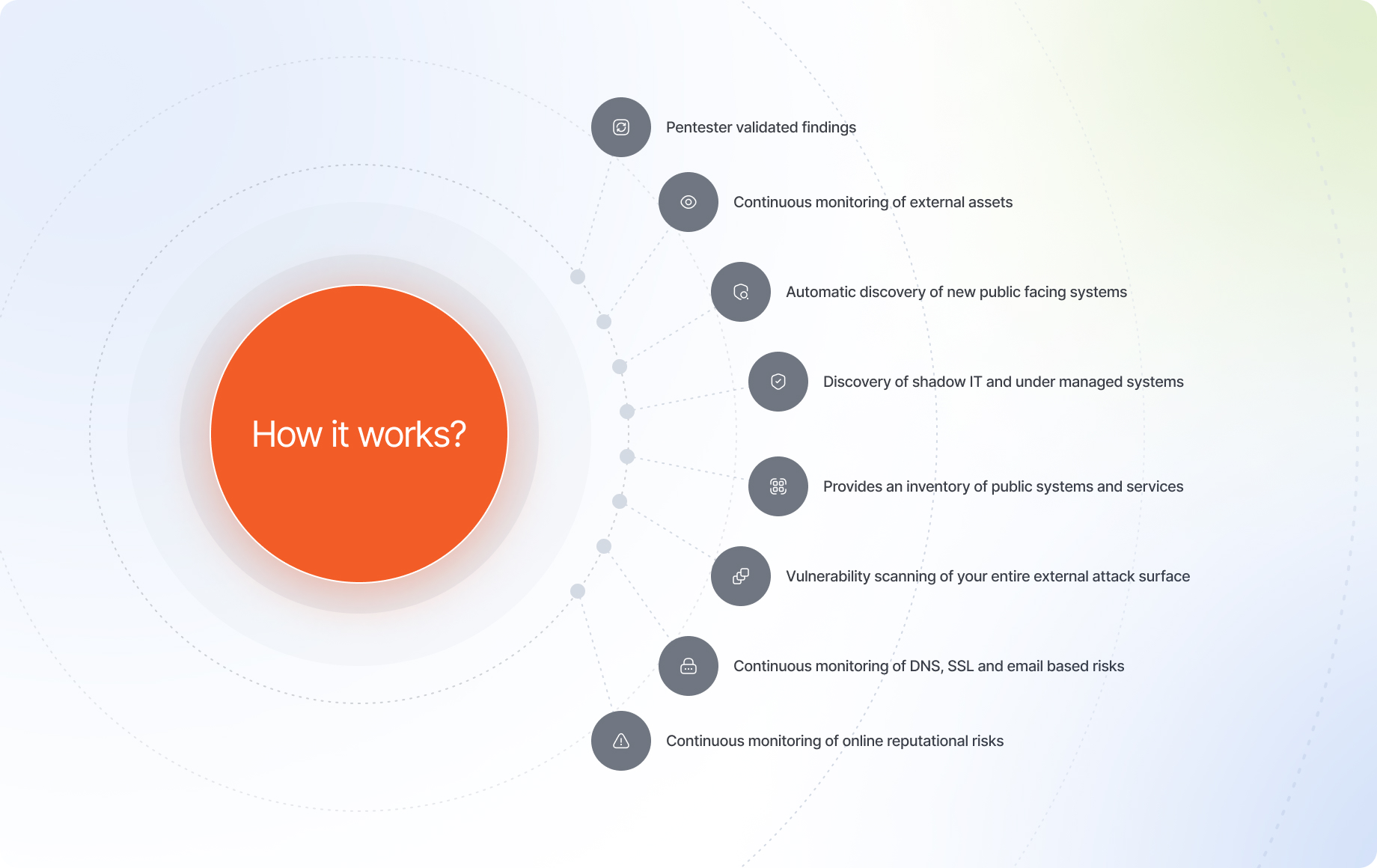
CASM safeguards company applications, workflows, users, and client data against rising targeted attacks. This solution stands out by delivering tangible benefits to your organization, such as:
Alerting you quickly to changes in your attack surface. Including finding accidental exposures and unmanaged assets that may be missed
Locating high-risk exposures tin public-facing assets
Providing a full external inventory of assets, risks, and confirmed vulnerabilities
Quickly validating changes and remediation efforts
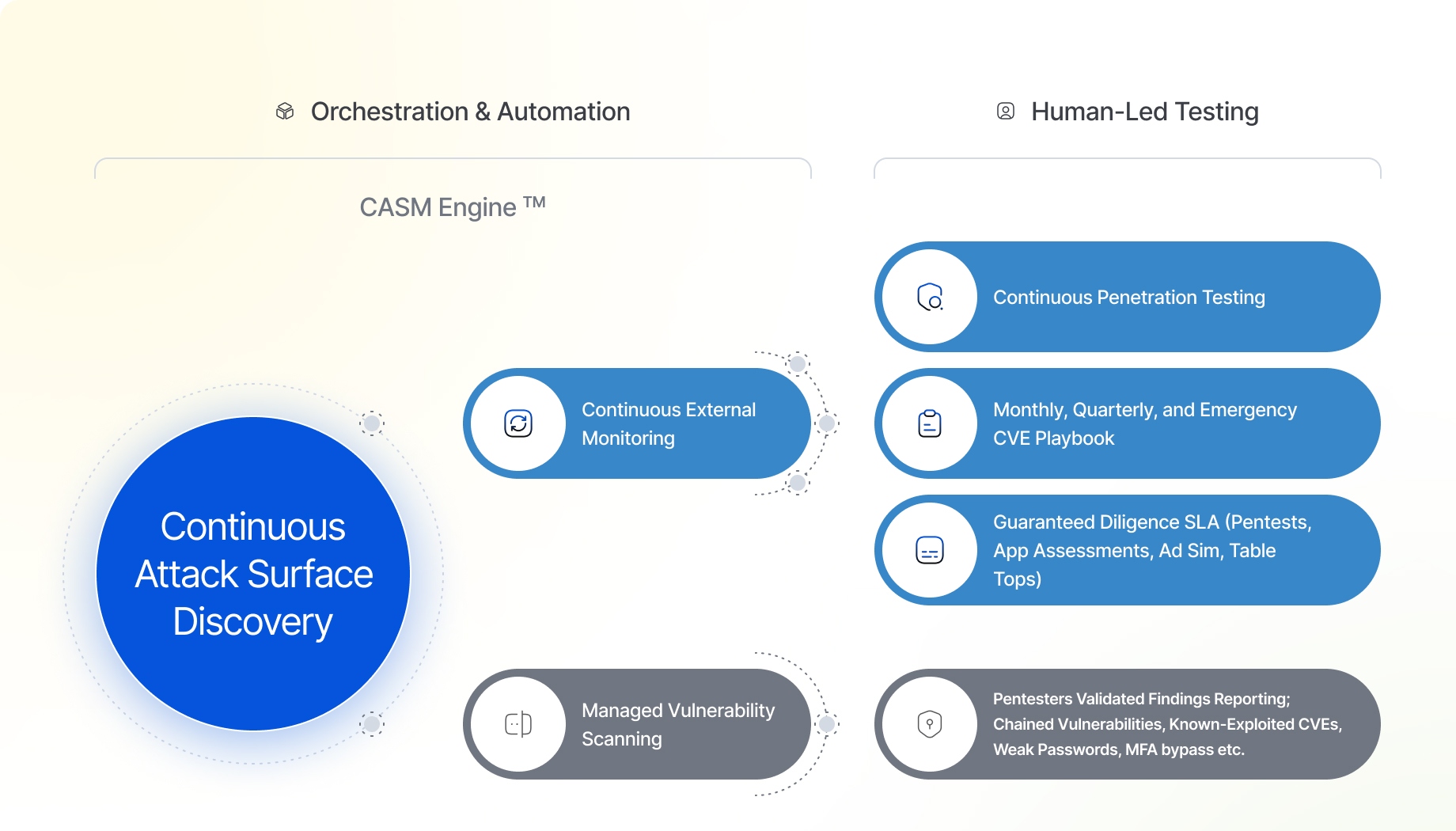
What CASM Does for Your Cybersecurity
Uncover, Inventory, and Protect
CASM Engine finds 75% more assets than other organizations, giving you complete visibility and 24/7 protection.
Actionable and Validated Alerting and Reporting
Our SaaS platform enables automatic reporting that delivers detailed, accurate readouts across multiple user types.
Defends Your Digital Assets
We give a hacker’s perspective of your attack surface showing the known and unknown vulnerabilities before the real hackers can find them.
Answering Your Questions:
CASM
What is Continuous Attack Surface Management?
CASM is a SaaS solution that orchestrates and automates critical security processes across your entire attack surface, or all of the parts of your organization’s system that could create or allow risk. By covering your entire attack surface (from laptops to IoT devices, email to cloud and more), CASM significantly reduces the time it takes to detect and respond to risks.
What’s more, our highly effective CASM solution automatically and continuously discovers assets, assesses risk, and reduces or even eliminates human effort in measuring and reporting risk. This creates a hands-off, highly effective, and expert-enabled solution designed by penetration testers (“pentesters”) to deliver the visibility and risk management your entire security and compliance team needs to be successful.
What are the main benefits of Continuous Attack Surface Management?
CASM works autonomously and automatically to continuously locate new assets, servers, and services (including the cloud!), freeing up your team to achieve more in the same 24 hours than they could before. Acting as an extension of your own team, CASM alerts you to vulnerabilities and advises on mitigation measures so that you beat hackers to the punch.
And with seamless integrations with popular cloud providers like Amazon Web Services, Microsoft Azure, and Google Cloud—even Slack channel notifications–our solution adapts to and accelerates the pace at which your security team can act to defend your network.
Who is a good candidate for CASM?
CASM is a great fit for organizations who are challenged with keeping up with the volume, volatility, or regional distribution of their assets, including organizations with 10 to 10,000+ external (internet-facing) assets or a high degree of external system changes. Additionally, organizations migrating to the cloud or those looking to automate their external discovery and vulnerability management will benefit greatly from CASM.
How does CASM differ from managed vulnerability scanning?
Vulnerability scanning is essential and should run continuously if possible, weekly at a minimum. CASM provides the ideal continuous, automatic discover of new assets needed to get a full picture of what you’re monitoring. Built by pentesters, CASM is also designed to support SynerComm’s Continuous Penetration Testing (CPT) services. So when your requirements call for more than just scanning, CASM combined with CPT is an ideal solution.
Can CASM be combined with Continuous Penetration Testing?
It can, and it should be! CASM exists today because SynerComm’s experienced team of pentesters needed a reliable set of automated tools to support continuous discovery, monitoring and testing. Now five years since its creation, CASM still exists to support and continually improve our Continuous Penetration Testing capabilities.
Is there a difference between CASM and Continuous Vulnerability Management?
Continuous vulnerability management describes ongoing monitoring, testing, remediation, testing, etc. for vulnerabilities. Continuous vulnerability management is so important that The Center for Internet Security CIS Critical Security Controls lists it as their #7 most critical control. The great news: CASM is the fastest and easiest solution for companies looking to achieve continuous (external) vulnerability management.
Will CASM fit into my existing security framework?
Yes! CASM fits into most frameworks’ requirements for inventory, change detection, and risk review processes. It was designed to agnostically support all popular standards.
What reporting formats are available with CASM?
Dashboard – CASM is a SaaS platform accessible by any modern web browser. In addition to viewing data and running/downloading reports, the CASM dashboard is used for administration.
Monthly – PDF attack surface reports can be delivered automatically or downloaded through the dashboard.
Findings – Findings are CASM’s most important notifications. CASM subscribers are alerted when a new finding needs attention.
API Integration – Not all roles require web-browser-based access to information. CASM’s APIs allow you to integrate into nearly any process or application, including Slack and ServiceNow.
What resources will I need to implement CASM?
Most of our CASM subscribers are up and running in less than 15 minutes, while required resources are often determined by how well our clients know their systems. Our first step will be scoping to make the process painless, as well as using our automated asset discovery to confirm or exclude systems as your team wishes. Once onboarded, CASM runs autonomously and is always ready when you need it.
Some roles benefit from regular research and monitoring of assets through CASM while others are completely hands-off unless they are responding to a finding.
How can I get started with Continuous Attack Surface Management?
We can start today, no investment required: click here for a no-cost cybersecurity assessment, then start your 14-day trial!