SynerComm and ChannelBytes hosted an engaging virtual discussion with Check Point, touching on topics ranging from “Innovative ways Check Point is tackling cloud security issues” to “How does...


SynerComm and ChannelBytes hosted an engaging virtual discussion with Check Point, touching on topics ranging from “Innovative ways Check Point is tackling cloud security issues” to “How does...

SynerComm and ChannelBytes hosted an engaging virtual discussion with Expel, touching on topics ranging from “Advancements from SIM technology” to “Email phishing and the cybersecurity...

See the original publication found in On Balance Magazine. At some point in 2015, cybercriminals had an aha moment. Instead of going through all of the trouble of breaking into a network, stealing...

SynerComm Inc. is proud to announce it has been named a 2020 “Overall” Partner of the Year by Juniper Networks. Selected out of 1,000 plus Juniper Networks North America Partners, SynerComm has been...

Another M365 email outage... seriously just Google it... there are even multiple websites that monitor and tell you there is an outage but there is nothing you can do about it… or is there? Whether...
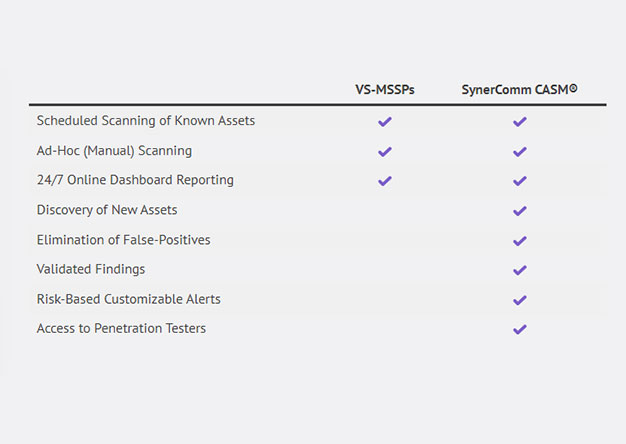
Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services. Seriously though, the following article will present the need for better external...

In penetration testing, it’s important to have an accurate scope and even more important to stick to it. This can be simple when the scope is limited to a company’s internet service provider (ISP)...

One of the things I have noticed while working at SynerComm over the years is that while most companies have employees on staff who possess the necessary technical knowledge to complete their...

Why Trust is Essential Our valuable experience is both deep and broad. We have extensive experience with IT infrastructure, security, operations, management, and logistics, allowing us to serve our...
SynerComm partnered with ChannelBytes to present 60 minute session where we discuss what it means to do quality, modern penetration testing in 2020. Penetration testing is a core part of the...