Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services. Seriously though, the following article will present the need for better external visibility and vulnerability management.
Whether you are vulnerability scanning to meet compliance requirements or doing it as part of good security practices, there is a universal need. At the time of this article, there are essentially three equally capable and qualified scanning solutions. They include products from Tenable, Rapid7 and Qualys. My point is that each of these scanning solutions, if configured correctly, should produce accurate and similar results. Therefore, as long as your scanning provider is using one of these three solutions, they should be able to detect vulnerabilities. SynerComm starts with a top scanner and then addresses all the gaps that your MSSP is missing.
Vulnerability scanning and analysis is a critical process within all information security programs. Scanners should find missing patches, dangerous configurations, default passwords, and hundreds of other weaknesses. Their technology is based on probing systems over networks and trying to determine if the system exhibits specific vulnerabilities. While the process itself isn’t complicated, many organizations choose to outsource it to a managed service provider. If you need a provider or already have one, it’s time to upgrade to Continuous Attack Surface Management (CASM™).
Ditch your Vulnerability Scanning MSSP
Vulnerability scanning MSSPs served their role well for many years but failed to keep up. They failed to keep with cloud migrations, failed to keep up with the rate of IT changes, and failed to provide tools that simplify and enable security for their subscribers.
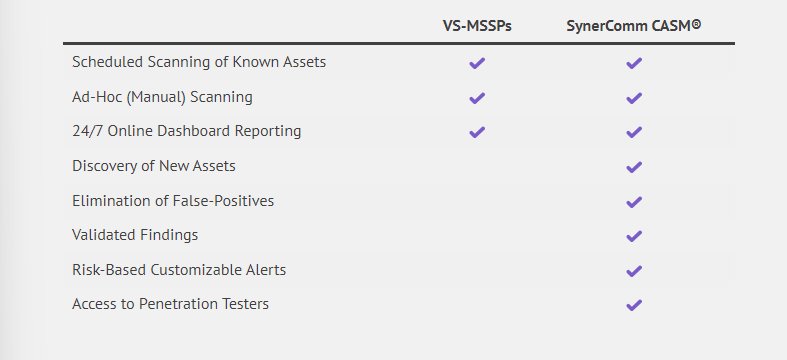
VS-MSSPs Lack Discovery of New Assets
SynerComm’s CASM Engine™ was designed by our pentesters to scour the internet looking for new systems and exposures. You can’t count on scan targets to be configured correctly all of the time, and most if not all VS-MSSPs fail to discover new systems. CASM® increases coverage and maintains an accurate asset inventory with automatic discovery.
VS-MSSPs are Plagued with False Positives and Fail to Accurately Describe Risk
CASM® virtually eliminates false positives through our Findings-Based Reporting. False positives are inherent to non-privileged scanning, especially when targets are located behind firewalls and threat prevention controls. Our analysts validate all vulnerabilities before publishing a finding to ensure you’re only notified when it matters.
Raw vulnerability scan results are always available to review and download, but findings are reserved for vulnerabilities that create real risk to your business. SynerComm’s pentesters ensure that a vulnerability is exploitable and could cause harm to your organization before reporting it. Say goodbye to “nuisance vulnerabilities” being tracked like real findings.
VS-MSSPs Lack Security Expertise
The value of most vulnerability scanning MSSPs begins and ends with their automation. SynerComm’s CASM® subscriptions evolved from the need for more accurate scanning and reporting plus the requirement of continuous discovery. We’ve scripted and improved everything that can be automated, but still have a team of pentesters analyzing vulnerabilities.
Unlike VS-MSSPs, SynerComm has a whole suite of assurance and validation services for clients also needing penetration testing and other assessments. Most CASM® subscriptions are paired with Continuous Penetration Testing to provide complete coverage against both known and unknown threats.
The benefits of Continuous Attack Surface Management include:
- Accurate external asset inventory
- Automatic discovery of new Internet-connected assets, no need to continually update scan configurations
- Continuous monitoring for changes in services and vulnerabilities
- Cloud savvy with integrations into AWS, Azure and more
- No false positives
- Findings based on actual business risks
- Dashboard access to view your entire external attack surface including:
- Raw vulnerability scan results and reports
- DNS, Whois, GeoIP for all discovered assets
- Screenshots of web services (easier identification)
- Service and OS fingerprinting
- Domain and subdomain enumeration
- Breaches affecting employee email accounts
- API integration into 3rd party alerting and ticketing systems
If you’ve ever wondered what your systems and exposures look like to a cyber-criminal, just ask a pentester. SynerComm’s CASM® Engine was originally designed to provide accurate and timely reconnaissance information to our penetration testers. Access to this data and our ‘Findings-Based Reporting’ is available to all CASM® and Continuous Penetration Test subscribers.
Learn more about our Continuous Attack Surface Management and our industry-leading Continuous Penetration Test subscriptions.