ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result, there’s some new features we’d like to introduce.
Cleaner User Interface
We’ve cleaned up the number of arguments required to run the app from 6 to 3. Now you only need to specify the AMI KEY, AMI ID, and the number instances you’d like start. You can still specify images size, type, etc, we just set the most cost effective options as default.
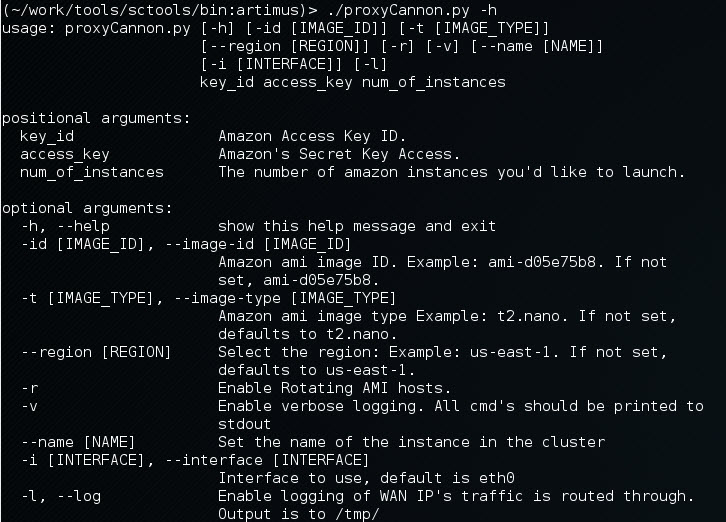
New Options
So if you’re familiar with the older version of createProxy, you’ll notice we’ve added new options.
- The -v option provides verbose debug output, specifically used for troubleshooting issues.
- The -i option was added to let the user specify which interface should be used for establishing outbound connections. Useful if your client is on a mac, or has multiple nic’s.
- The -l option will log all assigned IP’s to a file for record keeping
- The -r switch rotate IP’s
Rotate IP?!
So even by sending your Nessus scans across 10 Amazon EC2 hosts an IPS can still detect and shun one of your exit nodes. To deal with this, we’ve added the -r feature which will automatically rotate the public IP address of every exit node. Let say for example you fire up proxy cannon with 10 nodes and add the -r switch. The first thing the script will do is build the egress nodes, tunnels, iptables and routes like normal. Next the script will choose one node (at random) and alter the local route table to make that it appear less appealing than the other 9. As a result, all new outbound TCP/UDP/ICMP packets will be traverse the remaining 9 nodes evenly all the while allowing any existing session data on the chosen node time to finish receiving its data. The script will then monitor the network state table for the chosen node. Once it identifies that the node is idle (i.e. no half open TCP/UDP/ICMP packets), proxyCannon tells Amazon to re-assign the nodes WAN IP. Next ProxyCannon will reprovision the host and add it back into the general pool of 10 nodes, and move onto the next. On average, regardless of the number of exit nodes provisioned, proxyCannon will change its exit nodes IP’s about 30 times in one hour without dropping / breaking a single session!
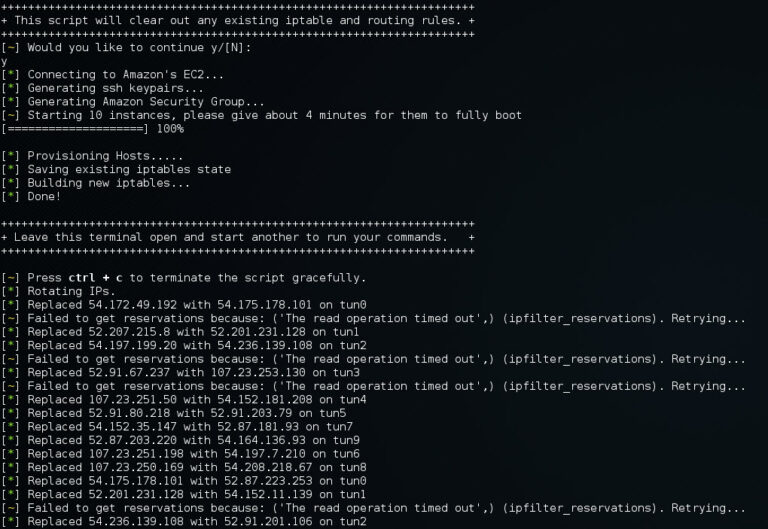
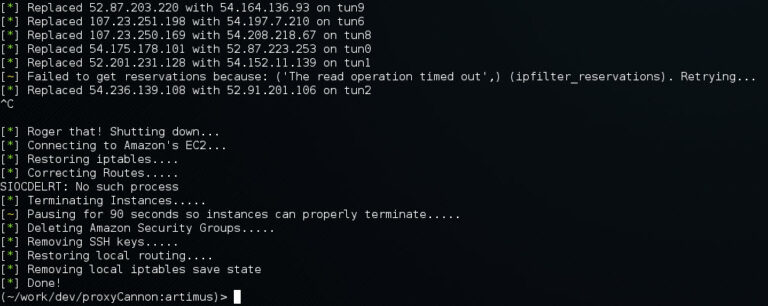
Rotate Nodes (-r) in action. You’ll note a few AWS API timeouts. Proxy Cannon will now attempt to recover its state automatically without immediately giving up.
Save iptables state
ProxyCannon makes use of iptables to do its natting. In the past, if you ran it, your previous iptables state (if any) was lost. With this update, your previous iptable state will be saved before running, and restored when finished.
Better Signal handling
We’ve added better (not perfect) signal handling, so that if/when an issue arises, ProxyCannon will attempt to cleanup up gracefully, restoring your system to its previous state.
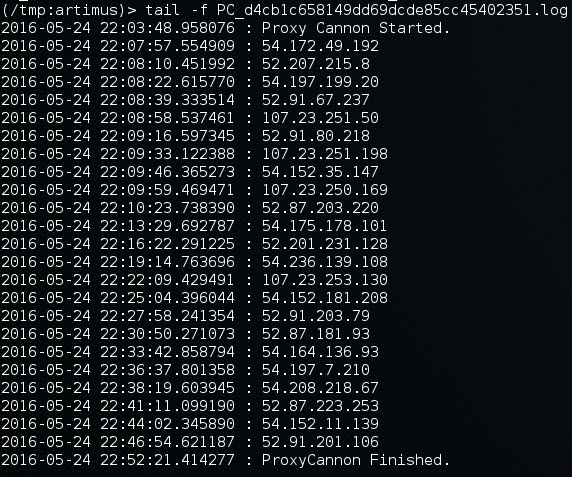
WAN IP Logging
If you ever want to know what WAN IP’s your traffic took you can use the -l switch to record a log to the /tmp directory.
Conclusion
Take a look and try it out. If you run into any problems please reach out to SynerComm.
@jarsnah12


